주말을 맞이하여, naver.how 에 대하여 ssllabs.com 점검을 실시했다.
#보안점검

Home Projects Qualys Free Trial Contact
You are here: Home > Projects > SSL Server Test > naver.how
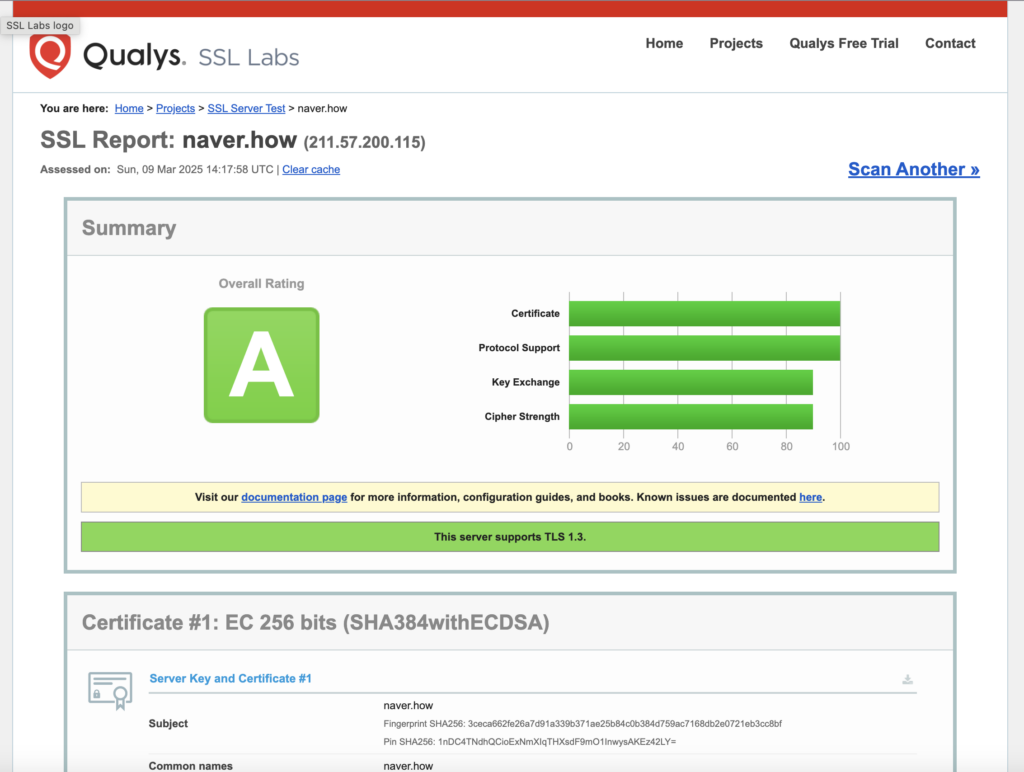
SSL Report: naver.how (211.57.200.115)
Assessed on: Sun, 09 Mar 2025 14:17:58 UTC | Clear cache
Summary
Overall Rating
A
0
20
40
60
80
100
Certificate
Protocol Support
Key Exchange
Cipher Strength
Visit our documentation page for more information, configuration guides, and books. Known issues are documented here.
This server supports TLS 1.3.
Certificate #1: EC 256 bits (SHA384withECDSA)
![]()
| Server Key and Certificate #1 | |
| Subject | naver.how Fingerprint SHA256: 3ceca662fe26a7d91a339b371ae25b84c0b384d759ac7168db2e0721eb3cc8bf Pin SHA256: 1nDC4TNdhQCioExNmXIqTHXsdF9mO1InwysAKEz42LY= |
| Common names | naver.how |
| Alternative names | cp.naver.how naver.how |
| Serial Number | 04b4e9206175b4e0be977618c410abfb1e3d |
| Valid from | Sat, 18 Jan 2025 14:54:44 UTC |
| Valid until | Fri, 18 Apr 2025 14:54:43 UTC (expires in 1 month and 9 days) |
| Key | EC 256 bits |
| Weak key (Debian) | No |
| Issuer | E5 AIA: http://e5.i.lencr.org/ |
| Signature algorithm | SHA384withECDSA |
| Extended Validation | No |
| Certificate Transparency | Yes (certificate) |
| OCSP Must Staple | No |
| Revocation information | OCSP OCSP: http://e5.o.lencr.org |
| Revocation status | Good (not revoked) |
| DNS CAA | No (more info) |
| Trusted | Yes Mozilla Apple Android Java Windows |
![]()
![]()
Click here to expand
Configuration
![]()
| Protocols | |
| TLS 1.3 | Yes |
| TLS 1.2 | Yes |
| TLS 1.1 | No |
| TLS 1.0 | No |
| SSL 3 | No |
| SSL 2 | No |
![]()
| Cipher Suites | ||
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 (0xc02c) ECDH x25519 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca9) ECDH x25519 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_ECDSA_WITH_AES_256_CCM_8 (0xc0af) ECDH x25519 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_ECDSA_WITH_AES_256_CCM (0xc0ad) ECDH x25519 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_ECDSA_WITH_ARIA_256_GCM_SHA384 (0xc05d) ECDH x25519 (eq. 3072 bits RSA) FS | 256 | |
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b) ECDH x25519 (eq. 3072 bits RSA) FS | 128 | |
TLS_ECDHE_ECDSA_WITH_AES_128_CCM_8 (0xc0ae) ECDH x25519 (eq. 3072 bits RSA) FS | 128 | |
TLS_ECDHE_ECDSA_WITH_AES_128_CCM (0xc0ac) ECDH x25519 (eq. 3072 bits RSA) FS | 128 | |
TLS_ECDHE_ECDSA_WITH_ARIA_128_GCM_SHA256 (0xc05c) ECDH x25519 (eq. 3072 bits RSA) FS | 128 | |
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 (0xc024) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 256 | |
TLS_ECDHE_ECDSA_WITH_CAMELLIA_256_CBC_SHA384 (0xc073) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 256 | |
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 (0xc023) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 128 | |
TLS_ECDHE_ECDSA_WITH_CAMELLIA_128_CBC_SHA256 (0xc072) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 128 | |
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA (0xc00a) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 256 | |
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA (0xc009) ECDH x25519 (eq. 3072 bits RSA) FS WEAK | 128 | |
![]()
| Handshake Simulation | |||
| Click here to expand | |||
| (1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it. | |||
| (2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI. | |||
| (3) Only first connection attempt simulated. Browsers sometimes retry with a lower protocol version. | |||
| (R) Denotes a reference browser or client, with which we expect better effective security. | |||
| (All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE). | |||
| (All) Certificate trust is not checked in handshake simulation, we only perform TLS handshake. |
![]()
| Protocol Details | |
| Secure Renegotiation | Supported |
| Secure Client-Initiated Renegotiation | No |
| Insecure Client-Initiated Renegotiation | No |
| BEAST attack | Mitigated server-side (more info) |
| POODLE (SSLv3) | No, SSL 3 not supported (more info) |
| POODLE (TLS) | No (more info) |
| Zombie POODLE | No (more info) TLS 1.2 : 0xc023 |
| GOLDENDOODLE | No (more info) TLS 1.2 : 0xc023 |
| OpenSSL 0-Length | No (more info) TLS 1.2 : 0xc023 |
| Sleeping POODLE | No (more info) TLS 1.2 : 0xc023 |
| Downgrade attack prevention | Yes, TLS_FALLBACK_SCSV supported (more info) |
| SSL/TLS compression | No |
| RC4 | No |
| Heartbeat (extension) | No |
| Heartbleed (vulnerability) | No (more info) |
| Ticketbleed (vulnerability) | No (more info) |
| OpenSSL CCS vuln. (CVE-2014-0224) | No (more info) |
| OpenSSL Padding Oracle vuln. (CVE-2016-2107) | No (more info) |
| ROBOT (vulnerability) | No (more info) |
| Forward Secrecy | Yes (with most browsers) ROBUST (more info) |
| ALPN | Yes http/1.1 |
| NPN | No |
| Session resumption (caching) | No (IDs assigned but not accepted) |
| Session resumption (tickets) | Yes |
| OCSP stapling | No |
| Strict Transport Security (HSTS) | No |
| HSTS Preloading | Not in: Chrome Edge Firefox IE |
| Public Key Pinning (HPKP) | No (more info) |
| Public Key Pinning Report-Only | No |
| Public Key Pinning (Static) | No (more info) |
| Long handshake intolerance | No |
| TLS extension intolerance | No |
| TLS version intolerance | No |
| Incorrect SNI alerts | No |
| Uses common DH primes | No, DHE suites not supported |
| DH public server param (Ys) reuse | No, DHE suites not supported |
| ECDH public server param reuse | No |
| Supported Named Groups | x25519, secp256r1 (server preferred order) |
| SSL 2 handshake compatibility | No |
| 0-RTT enabled | No |
| 1 http://211.57.200.57/wp/ (HTTP/1.1 200 OK) |
![]()
| Miscellaneous | |
| Test date | Sun, 09 Mar 2025 14:16:10 UTC |
| Test duration | 107.958 seconds |
| HTTP status code | 200 |
| HTTP server signature | nginx/1.24.0 (Ubuntu) |
| Server hostname | – |
SSL Report v2.3.1
| Copyright © 2009-2025 Qualys, Inc. All Rights Reserved. Privacy Policy. | Terms and Conditions |
| Try Qualys for free! Experience the award-winning Qualys Cloud Platform and the entire collection of Qualys Cloud Apps, including certificate security solutions. |
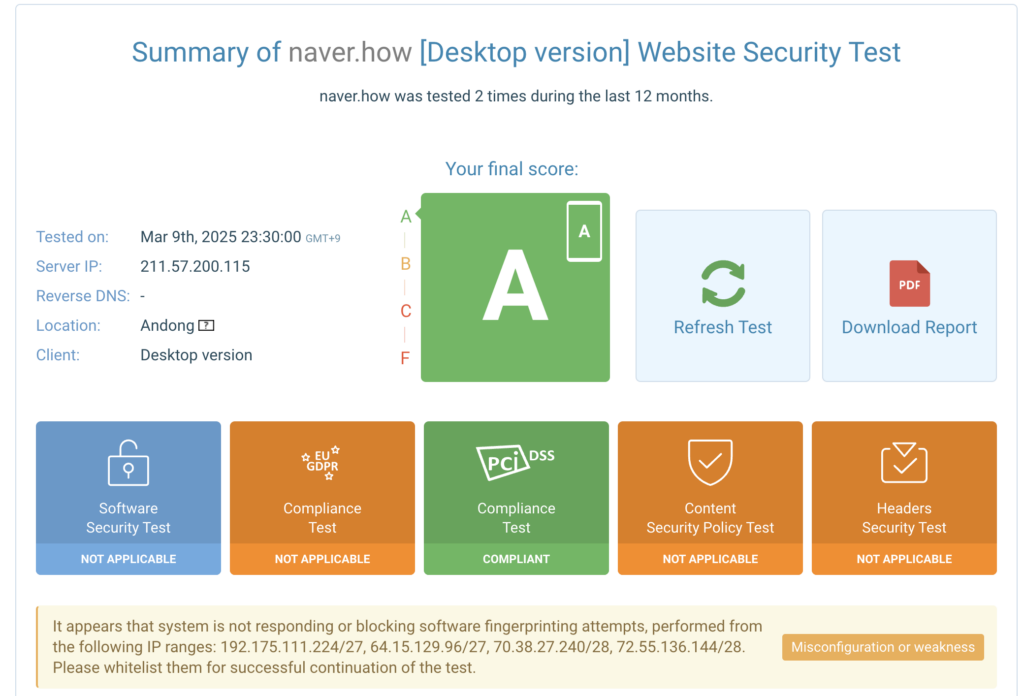
요건 https://www.immuniweb.com/ 테스트 결과
답글 남기기